Website repository that checks what sites your email address was used on were compromised.
The best Data Breach alternative to Data Breach Observatory is Have I Been Pwned, which is free. If that doesn't suit you, our users have ranked more than 25 alternatives to Data Breach Observatory and 14 are Data Breach Tools so hopefully you can find a suitable replacement. Other interesting Data Breach Tool alternatives to Data Breach Observatory are Mozilla Monitor, DeHashed, BreachDirectory and LeakCheck.
Website repository that checks what sites your email address was used on were compromised.

Mozilla Monitor arms you with tools to keep your personal information safe. Find out what hackers already know about you and learn how to stay a step ahead of them.
DeHashed is the largest & fastest data breach search engine. You can search for IP address, email, username, name, phone, VIN, address, and more! We have true wild card, dork usage, and we offer a real search engine experience! It's also free!.
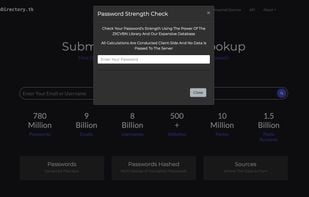
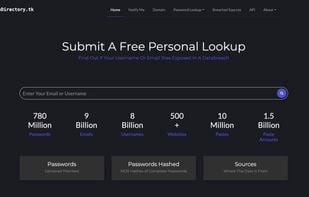
BreachDirectory allows you to search through all public data breaches to make sure your emails, usernames, passwords, and domains haven't been compromised.
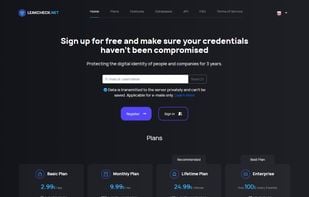
LeakCheck offers a search engine with a database of more than 7 billion leaked records. Users can search for leaked information using email addresses, usernames, phone numbers, keywords, and domain names. Our goal is to safeguard the data of people and companies.
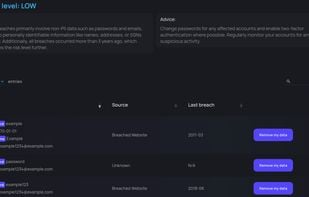
LEAK Tracker is a simple application built with Node.js and Express.js will enable you to create monitors for your passwords, email addresses and others which will warn you if some private information have leaked on the Web.
OSINT Investigation tool for advanced searches using Phone Numbers, Emails, and more. Secure, fast, and precise analysis for your Investigations.
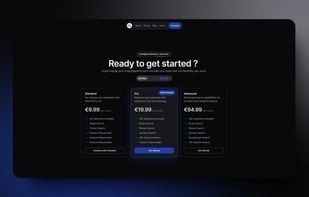
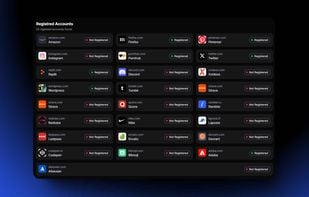
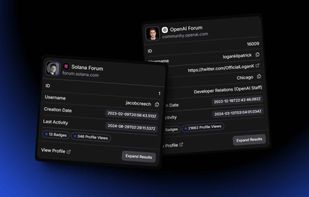
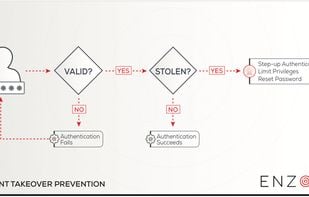
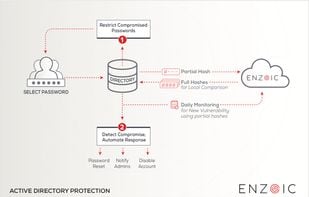
Enzoic provides solutions to detect compromised credentials and prevent attackers from unauthorized access accounts. With an Active Directory plugin and APIs, your organization is protected without any unnecessary friction to the user experience.
With expertise developed at the cybercrime intelligence division at the prestigious 8200 cyber unit at the IDF, Hudson Rock’s powerful cybercrime threat intelligence feed provides invaluable data for infrastructure protection, end-user protection, and supply chain risk...
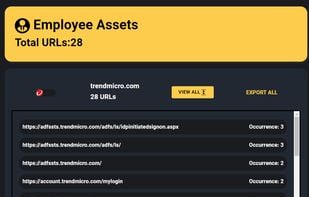
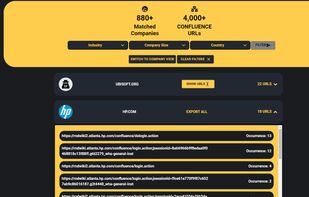
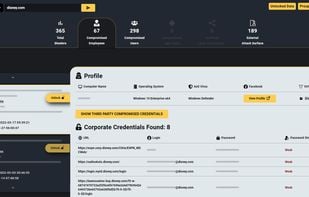
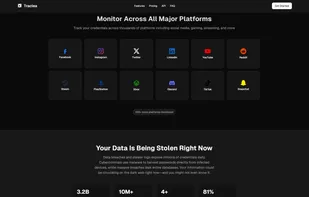
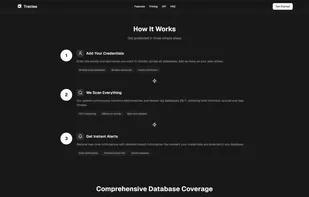
Traclea provides comprehensive real-time credential monitoring for both data breaches and infostealer malware. Unlike traditional breach checkers that only track corporate leaks, Traclea monitors 2,000+ breaches and 50+ active infostealer malware families (RedLine, Raccoon...

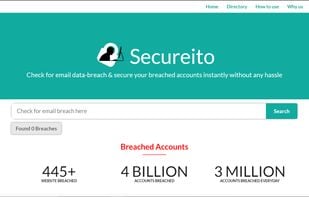
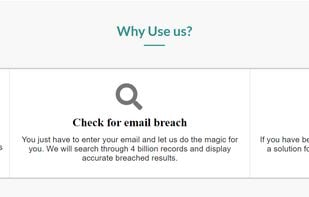
Check for Email data-hack & secure your hacked accounts instantly in one click. It generally takes a lot of time & manual efforts in securing all your accounts. With secureito, Users can secure their hacked accounts in a second.
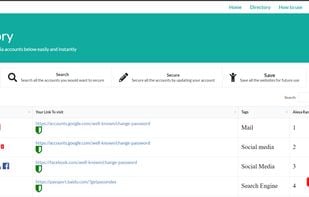
PassSafe protects people around the world by reporting more than 4,196,958,468 leaked encrypted information worldwide.