ThreatAware
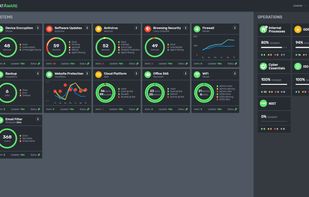
Cyber Hygiene Management platform designed for Cloud environments. It automatically creates an inventory of your endpoints which are connected to your cloud services, then highlights their cyber hygiene risks in a simple red, amber, green display.
Cost / License
- Subscription
- Proprietary
Platforms
- Software as a Service (SaaS)
Features
Tags
- Cybersecurity
- cyberhygiene
- endpoint-management
ThreatAware News & Activities
Recent activities
ThreatAware information
What is ThreatAware?
ThreatAware connects to your existing Cloud apps, Cloud managed networks and cyber security tools via API. Once connected it performs a cyber hygiene health check on each of the apps, networks and tools.
The unique aspect of ThreatAware it is automatically generates a real-time inventory based on the computers that are accessing your cloud apps, data and networks. This means that if you have home users, using home computers to accessing company data, they are add to the inventory and the same cyber hygiene checks are performed.
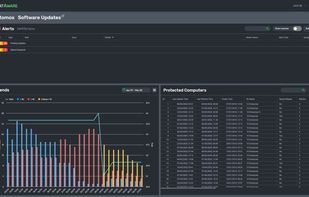
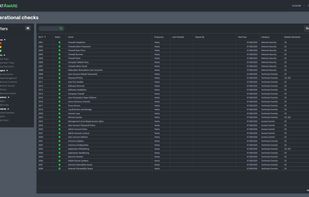
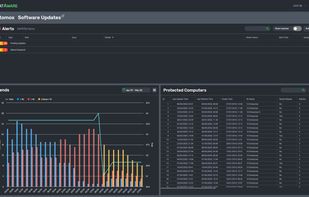
Any issues that ThreatAware finds from a cyber hygiene perspective it flags as alerts which can be assigned to your team. For example if you have a computer that is unencrypted, an alert will be generated. As soon as the machine has been encrypted, on the next poll ThreatAware will verify and then mark as complete if it has successfully verified as encrypted.
This agentless approach gives you full visibility of your cyber hygiene risks within minutes. This removes any concerns that you have team members accessing company data are doing so from protected computers.