Cost / License
- Paid
- Proprietary
Platforms
- Self-Hosted
- Software as a Service (SaaS)

ANET SureLog SIEM consolidates log source event data from thousands of devices endpoints and applications distributed throughout a network. It performs immediate normalization and correlation activities on raw data to distinguish real threats.
Measure your Website Performance for free. Track your metrics and get instant alerts with tips to increase your Online Reputation score. Your Online Reputation matters
msX Guard is a global, publicly accessible database of dangerous and unsafe domains, developed by Ixavence Bagart. It helps developers, browsers, and search engines detect and block phishing, malware, and scam websites before users interact with them.

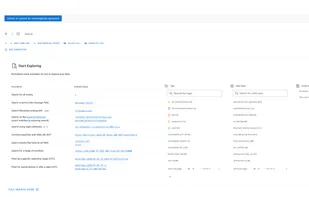
Timesketch is an open-source tool for collaborative forensic timeline analysis. Using sketches you and your collaborators can easily organize your timelines and analyze them all at the same time. Add meaning to your raw data with rich annotations, comments, tags and stars.
Free threat intelligence platform that aggregates 4000+ cybersecurity sources, clusters related articles, and delivers daily digests on APTs, ransomware, CVEs, and emerging threats.
At CheckMyCreds, we provide a platform that helps users quickly identify if their email credentials have been exposed in data breaches.
The industry's leading privacy-oriented threat intelligence and file reputation solution. Available via AWS cloud, or locally hosted in your environment. Full support available for private network deployments.
Lupovis provides precise, high-fidelity threat identification with a drastically reduced alert to noise ratio through a SaaS Decepetion as a Service platform.
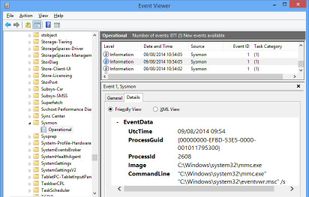
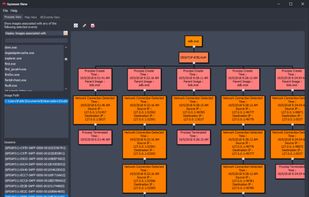
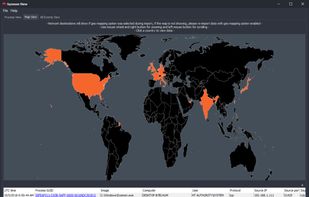
Sysmon View: an off-line Sysmon log visualization tool. Sysmon View helps in tracking and visualizing Sysmon logs by logically grouping and correlating the various Sysmon events together, using existing events data, such as executables names, session GUIDs, event creation time...
CLEARPHISH INC, is a provider of Hyper-Realistic Phishing Simulations and Highly Impactful Cinematic Mode Cyber Awareness Training.

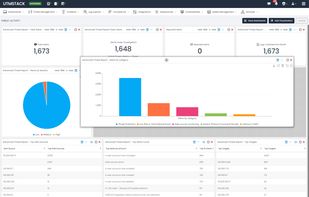
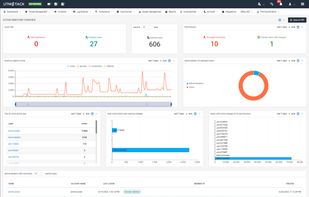
Threat Detection and Response, SIEM and Compliance Solution powered by Threat Intelligence, AI, and Real-time correlation.

FraudGuard.io provides cutting-edge APIs for IP reputation and threat intelligence, leveraging vast networks of honeypots and advanced analytics to deliver real-time, actionable insights. Our scalable platform helps businesses combat fraud, mitigate cyber risks, and stay ahead...
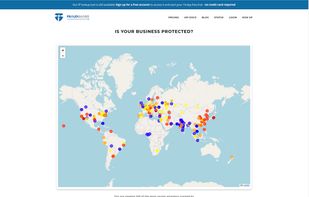
OpenText™ Threat Intelligence (BrightCloud) is a powerful cybersecurity solution that harnesses the power of machine learning and massive data sets from millions of real-world endpoints, leveraging a global sensor network to detect emerging threats and vulnerabilities.
threatYeti is a search engine for domain and IP threat intelligence, provided by alphaMountain. threatYeti expedites threat investigations and incident response for cybersecurity analysts and threat researchers.
Continuously identify vulnerabilities and simulate attack scenarios across your digital assets so you're always a step ahead.
With SmartIP you can enrich any IP address with geolocation data, ASN and hostname information, enforce GDPR compliance, assess potential risks and much more.
Dark Web Monitoring for MSSP. Budget-friendly and technically advanced darknet threat intelligence solution. Real time alerts and automated reports.
Defused provides plug-and-play capacities for internal detection of security incidents using decoys.
Cybersecurity company, offering interception of any content-based attack across collaboration channels including email, cloud storage, CRM apps, and messaging platforms. We prevent phishing, BEC, spam, malware, Zero-days, before it reaches users.
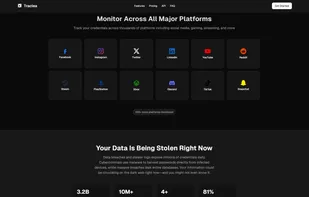
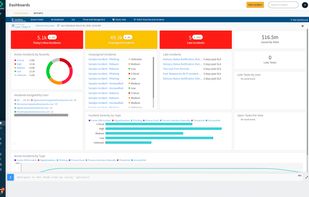
Traclea provides comprehensive real-time credential monitoring for both data breaches and infostealer malware. Unlike traditional breach checkers that only track corporate leaks, Traclea monitors 2,000+ breaches and 50+ active infostealer malware families (RedLine, Raccoon...