Cost / License
- Free
- Open Source (GPL-3.0)
Application type
Alerts
- Discontinued
Platforms
- Self-Hosted
- Sailfish OS
Molly is described as 'Independent Signal fork for Android' and is a instant messenger in the social & communications category. There are more than 100 alternatives to Molly for a variety of platforms, including Android, iPhone, Windows, Linux and Mac apps. The best Molly alternative is Signal, which is both free and Open Source. Other great apps like Molly are Telegram, Element, Matrix and Tox.
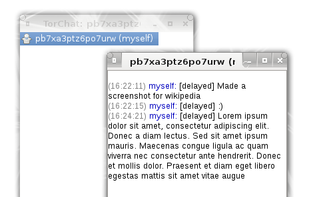
TorChat is a peer to peer instant messenger with a completely decentralized design, built on top of Tor's location hidden services, giving you extremely strong anonymity while being very easy to use without the need to install or configure anything.
A playful and interactive multimedia messaging app offering ephemeral photo and video sharing. Control view time, get alerts for screenshots, and engage with friends through gamified interactions and video calls.

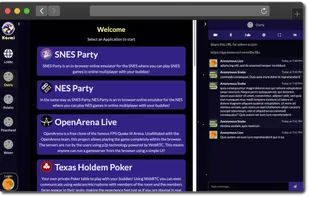
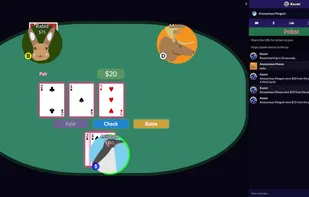
Kosmi is a free real time application and communication platform that offers voice, text and video calls along with games and applications such as SNES Party, NES Party, OpenArena, Poker, Virtual Cardtables, Synced YouTube and Cowatch Video.


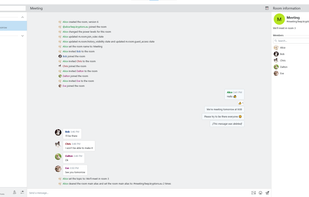
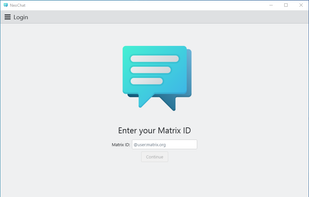
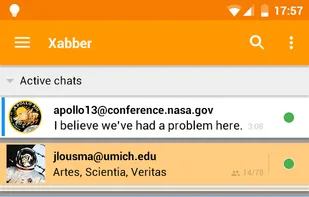
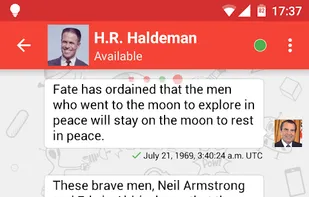
Safe, Fast And Decentralized Messenger.
Zangi Private Messenger is a decentralized messaging app with a focus on security and low data usage.

It uses the Tox protocol which is Peer to Peer, it will have a higher battery usage than other Messenger apps.
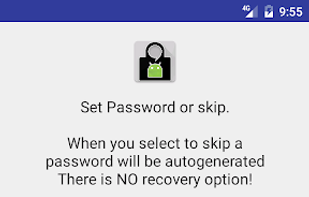
Technitium Mesh is a secure, anonymous, peer-to-peer (p2p), open source instant messenger designed to provide end-to-end encryption. Primary aim of developing this instant messenger is to provide privacy which is achieved using cryptography and anonymity using Tor network.
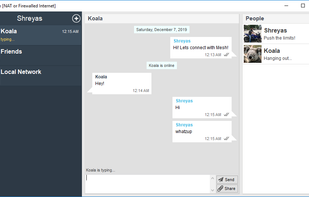
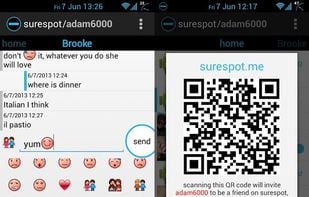
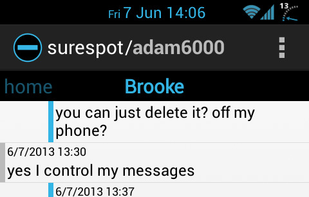
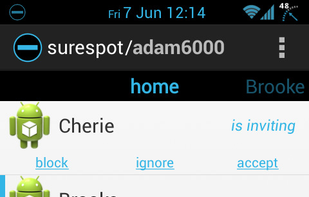
SureSpot is an open source encrypted messenger designed to make encrypted messaging simple and accessible to anyone.
Tinfoil Chat (TFC) is a FOSS+FHD peer-to-peer messaging system that relies on high assurance hardware architecture to protect users from passive collection, MITM attacks and most importantly, remote key exfiltration.