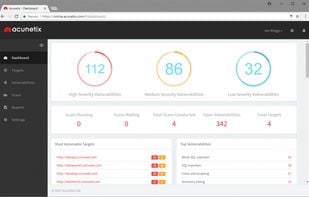
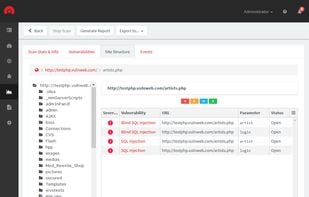
Audit your website security and web applications for SQL injection, Cross site scripting and other web vulnerabilities with Acunetix Web Security Scanner. Download Free Edition!
Zed Attack Proxy (ZAP) is described as 'The Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications' and is a penetration testing tool in the network & admin category. There are more than 25 alternatives to Zed Attack Proxy (ZAP) for a variety of platforms, including Windows, Linux, Mac, Web-based and iPhone apps. The best Zed Attack Proxy (ZAP) alternative is mitmproxy, which is both free and Open Source. Other great apps like Zed Attack Proxy (ZAP) are Fiddler, HTTP Toolkit, Burp Suite and Charles.
Audit your website security and web applications for SQL injection, Cross site scripting and other web vulnerabilities with Acunetix Web Security Scanner. Download Free Edition!



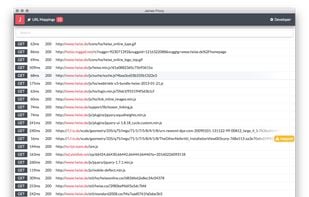
James is a HTTP Proxy and Monitor that enables developers to view and intercept requests made from the browser. It is an open-source alternative to the popular developer tool Charles.
Find security vulnerabilities right from your browser. Experience the next generation security tools without the need to install any additional software.


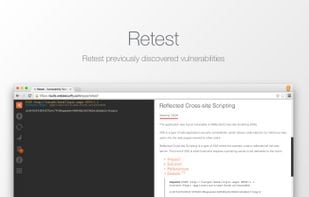
Human-in-the-loop penetration testing enhanced with AI. Identify vulnerabilities faster, reduce risk, and stay audit-ready with actionable reports and real-time visibility.
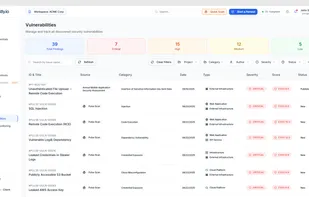
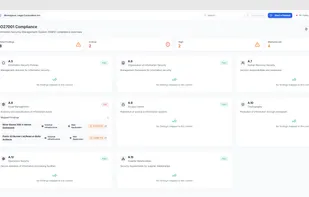
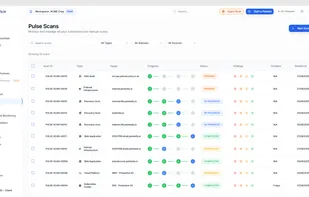
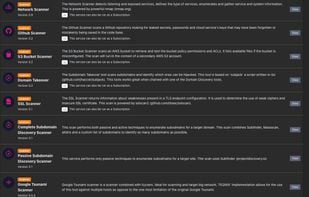
Guardius is a Software as a Service (SaaS) company designed to streamline and automate various IT needs for companies that operate their own websites or manage their own infrastructure. It is crucial for companies to safeguard their websites and infrastructure against potential...

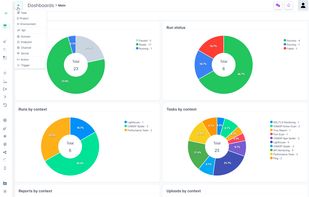
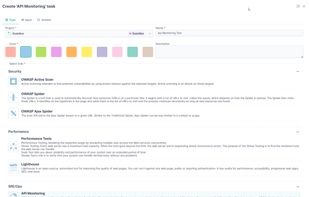
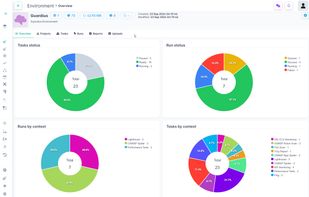
PENTESTON is a cloud-based Cybersecurity platform that allows you to oversee the complete secure development lifecycle of your application. It functions as a cyber security reporting and workflow management system, providing you with the necessary tools to manage the entire...
WHID Injector was born from the need for cheap and dedicated hardware that could be remotely controlled in order to conduct HID attacks. WHID stands for WiFi HID Injector. It is a cheap but reliable piece of hardware designed to fulfill pentesters needs related to HID Attacks...
A fully automated, active web application security reconnaissance tool. Key features: High speed: pure C code, highly optimized HTTP handling, minimal CPU footprint - easily achieving 2000 requests per second with responsive targets.
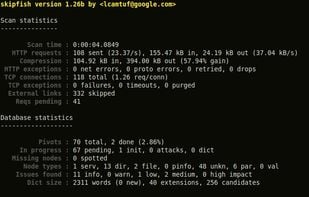

Firefox add-on that lets you change headers and request parameters before they're sent to the server. Unlike proxy request modifiers, it's integrated into the browser, so it has no problem with HTTPS connections, client authentication certificates, or other features that...

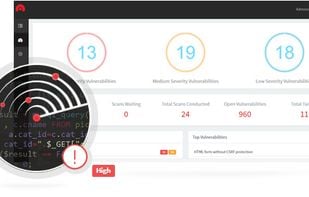
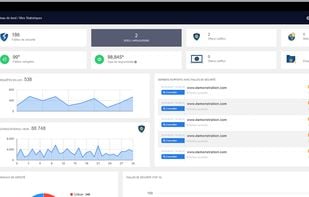
Put yourself in the shoes of a hacker! Without technical expertise, launch an audit to detect security flaws on your website or web application. Online website vulnerability scanner. No installation required. ISO & RGPD compliant. How to avoid hackers?
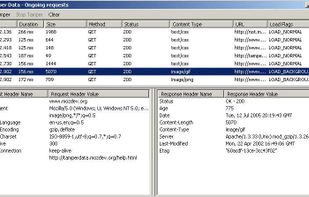
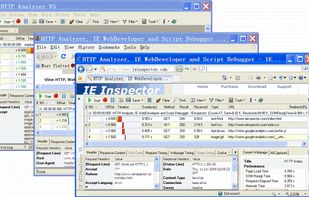
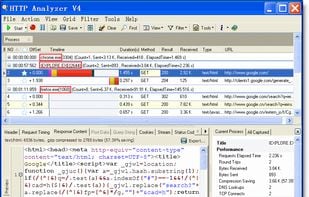
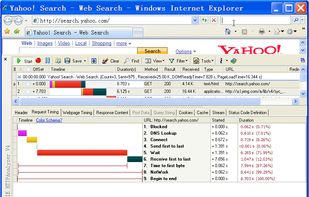
HTTP Analyzer is such a handy tool that allows you to monitor, trace, debug and analyze HTTP/HTTPS traffic in real-time. It is used by industry-leading companies including Microsoft, Cisco, AOL and Google.
TEQNIX is a platform with a number of tools and strategies for penetration testers, red teamers and secops. It promotes automation with scanners and utilities and also assist in a real-time attack situation.