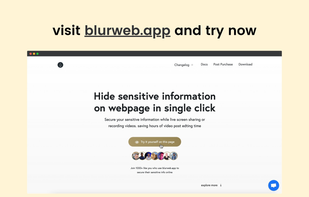
Free and easy to use website that allows handing over passwords, usernames, secure certificates, and other sensitive data to your friends and colleagues
Cost / License
- Free
- Proprietary
Platforms
- Online
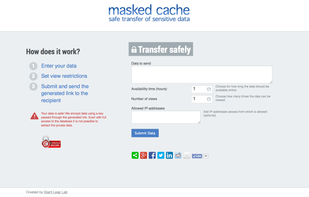
Free and easy to use website that allows handing over passwords, usernames, secure certificates, and other sensitive data to your friends and colleagues

Ellipticc Drive is an E2EE and PQC cloud drive with open-source frontend. Store, manage and share your files securely with anyone while having Dropbox-like UX but military grade encryption.
IBM® Security QRadar® SIEM consolidates log source event data from thousands of devices endpoints and applications distributed throughout a network. It performs immediate normalization and correlation activities on raw data to distinguish real threats from false...
A comprehensive Security Information & Event Management (SIEM) solution that enables cost-effective compliance and provides advanced security analytics to identify threats and manage risk, so you can protect your business.
A free, client-side tool to remove EXIF and metadata from images and documents without uploading files.
Drive Badger is a software tool for data exfiltration – which means, for copying data from the computer to external USB drive. But unlike many other tools from IT security area, Drive Badger is not a Proof-of-Concept kind of tool, bringing some groundbreaking techniques.


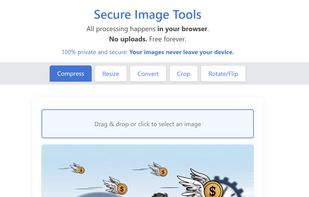
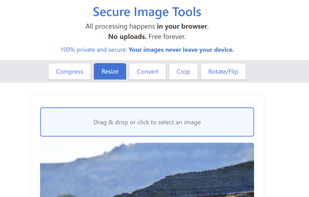
Secure Image Tools is a free, privacy-first suite of image tools in 34 languages. Instantly compress, convert, resize, and edit images — no sign-up, no watermarks, and your files are never stored. Fast, secure, and easy to use on any device.
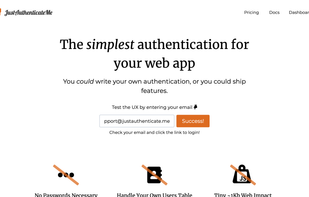
JustAuthenticateMe offers a simple authentication-as-a-service for your web apps. It uses magic links in emails as a way to verify identity so that neither you nor your users have to worry about passwords.

Every day, new breaches expose millions of credentials, and that puts your organization at risk of account takeovers and ransomware attacks. xonPlus changes the game by watching your email addresses and domains against fresh breach data, so you know the moment your data appears...


LocalKeys keeps your app secrets in a local, encrypted vault so you don’t have to store them in .env files. It runs entirely offline, uses strong AES-256-GCM encryption, and requires your explicit approval before any process can access a secret.
Download TU Latch, a second factor authentication (2FA) and authorisation (2FAuth) app that provides additional protection for your digital services with authorisation controls, TOTP access control and web browsing security from your computer.



TRESOR is a secure implementation of AES which is resistant against cold boot attacks. The basic idea behind this implementation is to store the secret key inside CPU registers rather than in RAM.
Traced is a free cybersecurity app for Android and iPhone. It detects suspicious activity from apps and unsecured Wi-Fi connections that might be used to spy on you or invade your privacy.
No hefty subscriptions. No annoying ads. 100% offline and private (no accounts/sign up). Fast, simple, yet powerful editor & scanner.




RevBits endpoint security solution protects every system in real-time, minimizing risk to threats. Know more about the RevBits endpoint security (EDR) solutions.
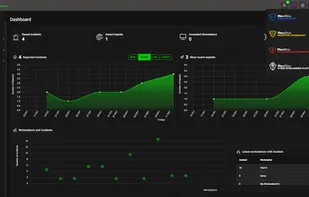
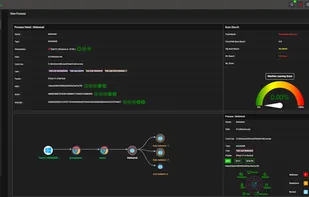
Understand your level of risk before a security breach occurs. Estimate your organization's FISASCORE® (Fiducial Information Security Assessment Score) for free and in minutes right now.

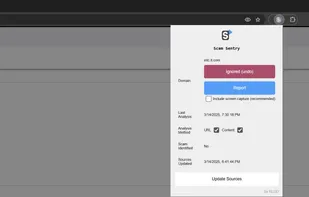
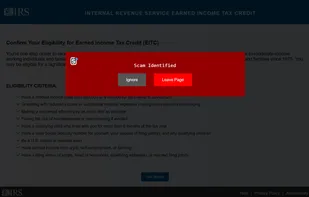
Scam Sentry is engineered to programmatically identify scams and fraudulent activity using advanced algorithms. Analysis is entirely automated and operates without storing your browsing activity.
NXT1 LaunchIT is the platform to build and run secure SaaS, automating cloud infrastructure for instant availability. Simply code and deploy. Secure by Design, it offers a direct path to FedRAMP-compliance readiness at a fraction of the traditional time and cost—out of the box.
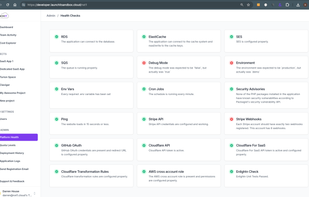
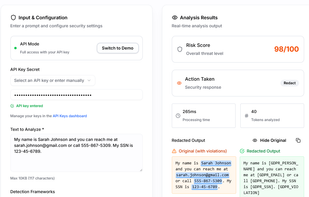
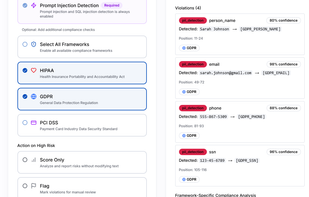
AI firewall that detects prompt injection attacks and redacts PII/PHI with compliance context (HIPAA, GDPR, PCI). Single API endpoint with sub-100ms response time.
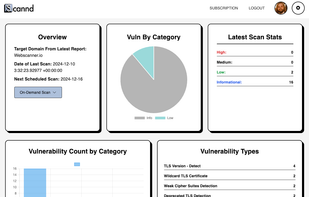
A powerful security scanning platform to identify, analyze, and mitigate vulnerabilities in your applications and infrastructure.
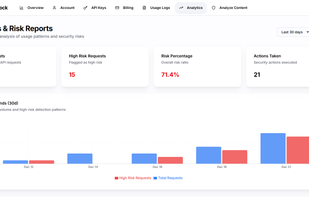
Information technology systems and applications produce a continuous stream of event and log details that can reveal suspicious behavior. Threat analytics offers the ability to proactively filter through huge amounts of data and identify real threats.
RedactMyPDF is an AI-assisted tool that automatically identifies sensitive information in PDFs, while giving users complete control to review, add, or remove redactions before downloading.
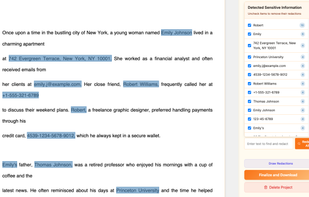
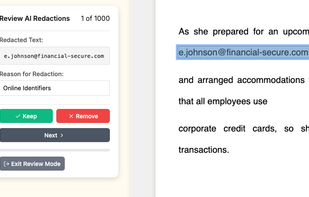
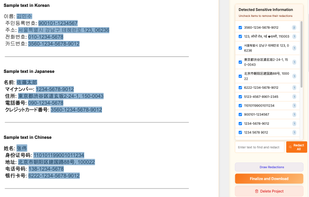
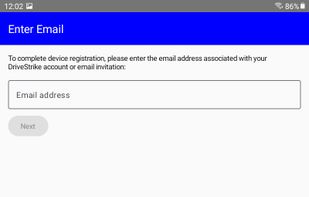
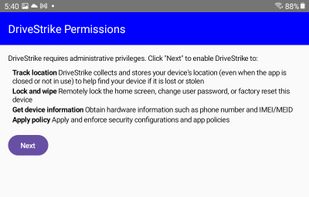
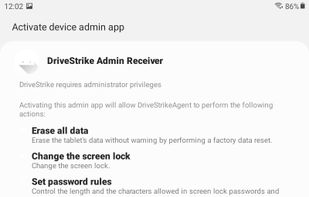
DriveStrike protects devices and data in the event of loss, theft, or use in remote locations. Remotely locate, lock, and wipe devices you manage to prevent data compromise.