Hasleo BitLocker Anywhere is described as 'The World's First BitLocker Solution for Windows 10/8.1/8/7 Home, Windows 8 Core and Windows 7 Professional Editions!' and is an app. There are more than 50 alternatives to Hasleo BitLocker Anywhere for a variety of platforms, including Windows, Mac, Linux, Android and iPhone apps. The best Hasleo BitLocker Anywhere alternative is VeraCrypt, which is both free and Open Source. Other great apps like Hasleo BitLocker Anywhere are Cryptomator, TrueCrypt, LUKS and AES Crypt.




LUKSUS is a tool that creates an encrypted volume and filesystem on a hardrive or other storage media as well as a filecontainer.
Zed! protects your personal and sensitive data in encrypted archives on e-mail, on USB sticks and in backups.
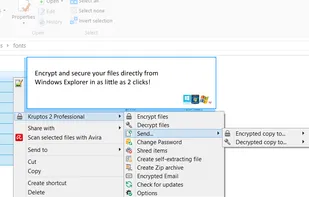
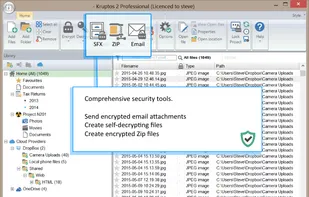
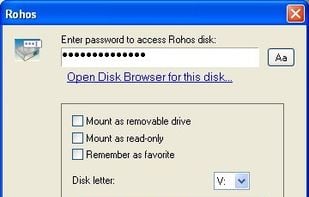
Rohos Mini Drive creates hidden and encrypted partition on the USB flash drive memory. You work with the files on the hidden partition without opening a special program. Those who have megabytes of sensitive files on the USB drive and seriously concerned with a data security...
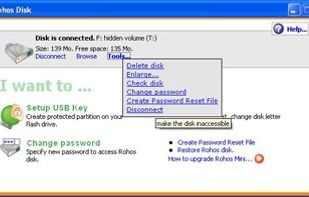
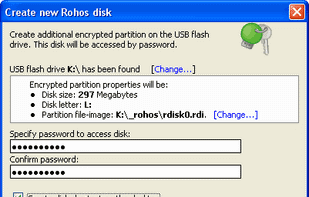
Its a software to encrypt and protect data with a password on your removable pen drives using the AES 256 bits encryption.
The Gostcrypt project has been launched at the end of 2013 as fork of the (late) Truecrypt project.
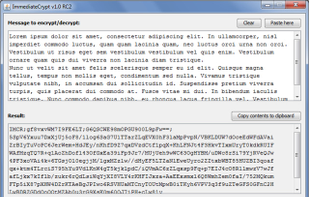
ImmediateCrypt is an utility for encryption and decryption of plain text messages with the AES-256 cipher.
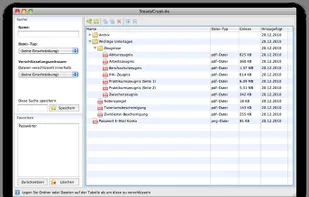
This is a Java-based application that allows the user to important files that are on that operating system to encrypt easy and secure and organize.
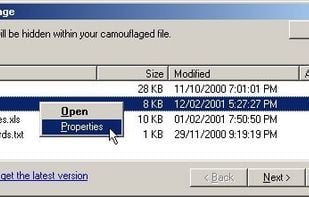
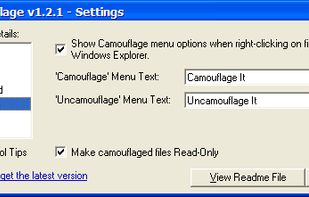
Camouflage allows you to hide files by scrambling them and then attaching them to the file of your choice. This camouflaged file then looks and behaves like a normal file, and can be stored, used or emailed without attracting attention.
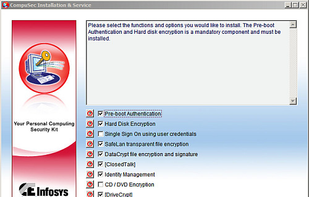
The FREE CompuSec is a PC Security Suite that protects Notebooks, Desktops and Tablet PCs by providing Access Control, Hard Disk Encryption, File Encryption, and Single Sign On. This Security software comes with a complete set of security functions for unlimited usage and...
Now this is what I call real security!... You may use any one of nineteen, industrial and military strength, encryption ciphers to secure your most precious private information.