Program to recover/crack SHA1, MD5 & MD4 hashes. Fastest SHA1/MD5 hash cracker on ATI and NVIDIA GPUs. World first multihash cracker for ATI.
Cost / License
- Free
- Proprietary
Platforms
- Windows
Program to recover/crack SHA1, MD5 & MD4 hashes. Fastest SHA1/MD5 hash cracker on ATI and NVIDIA GPUs. World first multihash cracker for ATI.
Cb Protection is a powerful positive security solution for data centers and critical systems that
A modern replacement for Sophos UTM based on Sophos, Cyberoam and Astaro technology combined.
LEAP is a non-profit dedicated to giving all internet users access to secure communication. Our focus is on adapting encryption technology to make it easy to use and widely available.

The best password recovery software program for recovering passwords to Facebook, Twitter, Google Plus, LinkedIn, MySpace, ebay, yahoo, gmail, hotmail, Badoo, aol, internet explorer, opera, firefox, msn messenger and more... SpotAuditor is password recovery software.
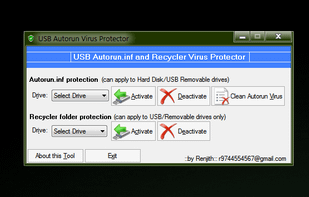
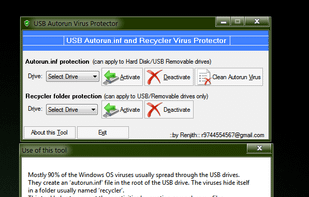
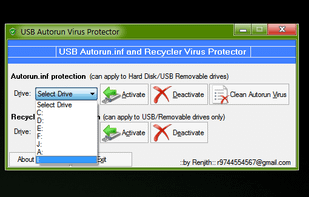
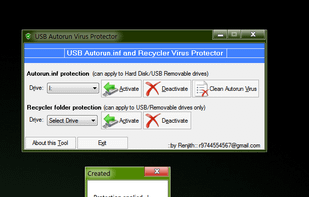
A simple and portable tool to protect USB storage drives against spreading of Autorun.inf viruses through the USB drives by creating some un-deletable dummy files in your USB drive.

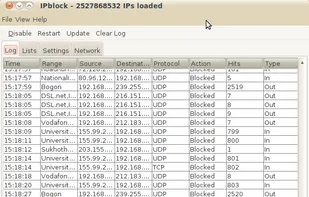
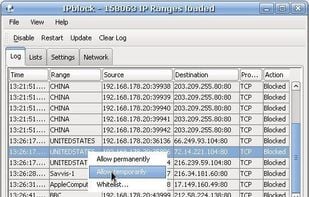
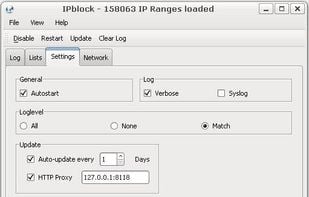
iplist is a Linux application for blocking connections to and from a specified range of hosts using the netfilter netlink-queue library. iplist is an open source IP filtering program similar to PeerGuardian .
Ory builds cloud-native authentication (login), authorization (permission), delegation (OAuth2, OpenID Connect), and user management software. You can deploy what you need yourself or use the Ory Network and get started in minutes.
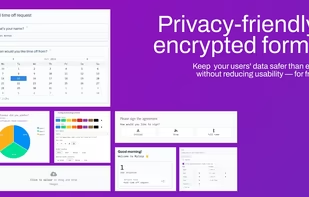
Build feature-rich end-to-end encrypted forms in minutes, completely free of charge. Prove your commitment to data security and appear more trustworthy than your competitors, while paying less for forms.
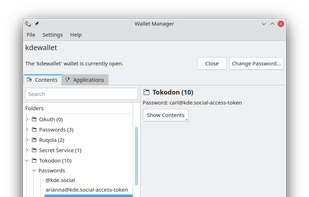
By using the Frameworks wallet subsystem it not only allows you to keep your own secrets but also to access and manage the passwords of every application that integrates with the wallet.
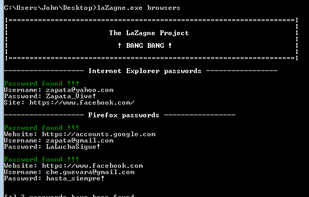
LaZagne is an open source application used to retrieve passwords stored on a local computer. Each software stores its passwords using different techniques (plaintext, APIs, custom algorithms, databases, etc.).
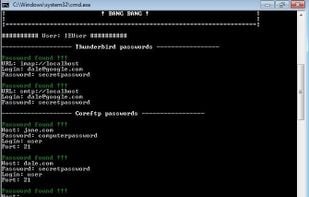
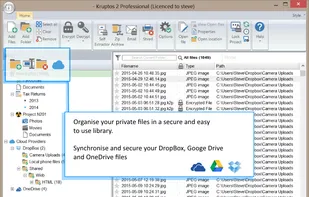
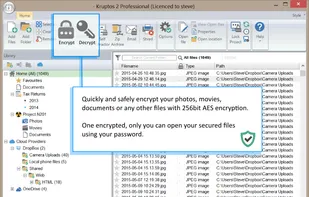
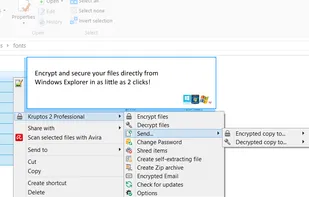
RatticDB is an open source Django based password management service. It has been designed from the ground up to be simple to use so that you can spend more time worrying about other things. Human being management has been simplified with a simple ACL scheme and a handy tool that...
Coupon codes and deals for Domain Names, Web Hosting, VPN, WordPress Themes and software.

Professional anonymity provider for secure anonymous email. Anonymous Domain and Hosting Offshore, Anonymous Surfing, SSL, Time Delayed, Bulk Email and many more functions.
Countermail is a web-based email service. It is hosted in Sweden. Its focus is on privacy. It provides several features, such as PGP support and diskless servers to protect users ability to communicate securely and anonymously.


Istio is an open platform for providing a uniform way to integrate microservices, manage traffic flow across microservices, enforce policies and aggregate telemetry data. Istio's control plane provides an abstraction layer over the underlying cluster management platform...
Gizlen.net - gizlenVPN offer VPN service with servers located in 24 countries. Assuming PPTP protocol. With support for Windows and Mac. As well as iOS and Android mobile devices.

SAASPASS is an Authenticator, Password Manager and a repository for Secure notes. It also secures access to computers such as Macs and Win with two-factor authentication. It can be used for personal use and/or by a company to secure their cloud apps.



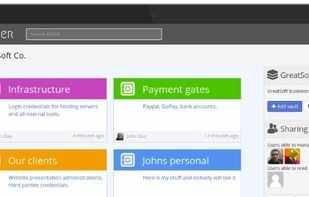
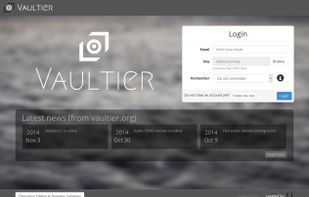
Open Source Enterprise software. Store your company data safely and share across your team!

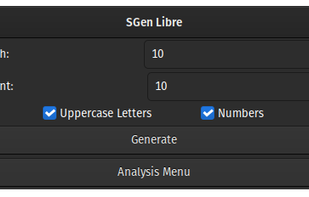
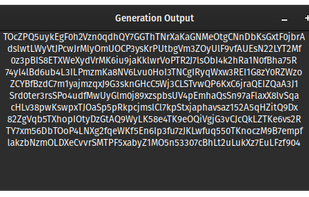
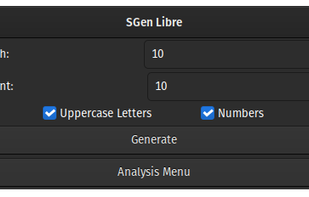
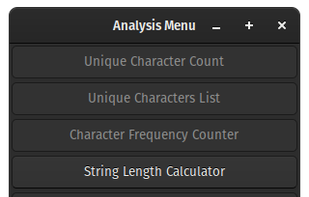
SGen Libre is a software toolkit used to generate, manipulate, and analyze random strings of information. SGen Libre is supposed to be used to generate passwords, but can also be used to generate information of any length.
Maltrail is a malicious traffic detection system, utilizing publicly available (black)lists containing malicious and/or generally suspicious trails, along with static trails compiled from various AV reports and custom user defined lists, where trail can be anything from domain...
Spyrix Employee Monitoring – is a modern solution for employees activity monitoring on PC.